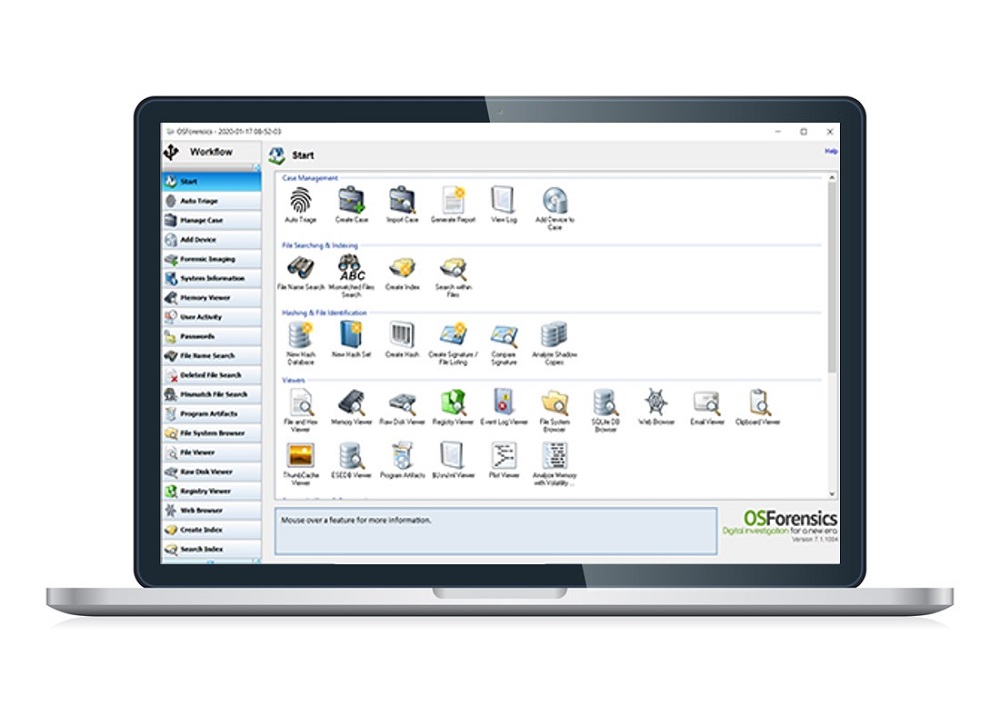
Description
OSForensics is a diagnostic tool that is also suitable for beginners due to its user-friendly structure. The forensics software is ideal for checking the integrity of data and tracking system changes.
Features
- Identify suspicious files and activities
- Quickly extract evidence from computers.
- Manage your investigations

Discover data
Discover relevant data faster with powerful file search and indexing. Extract passwords, decrypt files, and recover deleted files quickly and automatically from Windows, Mac, and Linux file systems.

Identify evidence
Identify evidence and suspicious activity with our hash matching and drive signature analysis capabilities. Identify and analyze all files and even automatically create a timeline of all user activity.

Manage your case
360° Case Management Solution. Manage your entire digital investigation with OSF's new reporting capabilities. Create custom reports, add narratives, and even attach reports from your other tools to the OSF report.
Complete suite for forensic investigations
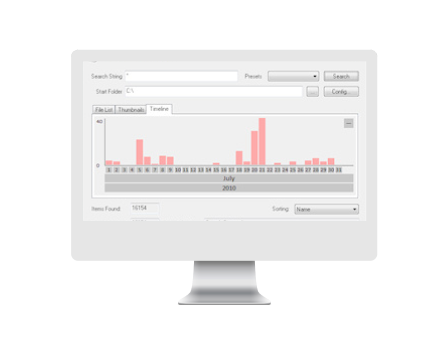
Search the contents of files with our highly acclaimed indexing engine that offers industry-leading relevance ranking, date range searching, exact phrase matching, "Google-like" context results, and more.


OSF provides powerful tools to detect and crack passwords on a live system or forensic image.
These include:
- Website logins and passwords (used in Chrome, Edge, IE, Firefox and Opera).
- Passwords for Outlook and Windows Live
- Stored WLAN passwords
- Password for Windows automatic login
- Windows and other Microsoft product keys
- Ports (serial/parallel)
- Network adapters
- Physical and optical drives
- Bitlocker detection
OSF also provides tools for cracking hashes using Rainbow tables and dictionary attacks.
OSF can expose the hidden HPA and DCO areas of a hard drive that can be used for malicious purposes, such as hiding illegal data.

Use OSF to access volume shadow copies. This allows you to see what a volume looked like at a certain point in the past and what has changed. You can detect changes to files and even view deleted files.

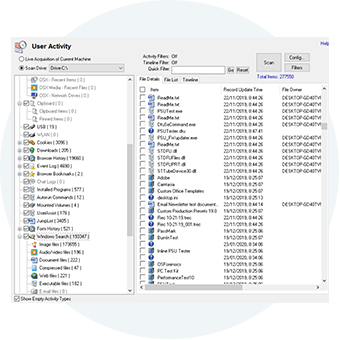
Identify suspicious files and activities

OSF offers a comprehensive suite of tools for analyzing files, emails and system information, including:
- File viewer that can display streams, hex, text, images and metadata
- Email viewer that can display messages directly from the archive
- Registry viewer for easy access to Windows registry hive files
- File system browserFile system browser for Explorer-like navigation through supported file systems on physical disks, volumes, and images
- Raw disk viewerRaw disk viewer for navigating and browsing raw disk bytes on physical disks, volumes, and images
- Web browserWeb browser for browsing and capturing online content for offline evidence management
- ThumbCache viewer to browse ThumbCache viewer to browse the Windows thumbnail cache database for evidence of images/files that may have once been on the system
- SQLite database browser to view and analyze the contents of SQLite database files
- ESEDB viewer to view and analyze the contents of ESE DB database files (.edb), a common storage format used by various Microsoft applications
- Prefetch viewer to identify the time and frequency of applications running on the system and thus recorded by the operating system's prefetcher
- Plist viewer to view the contents of plist files commonly used by macOS, OSX, and iOS to store settings
- $UsnJrnl viewer to view the entries stored in the USN journal, which is used by NTFS to track changes to the volume
Manage your digital investigations

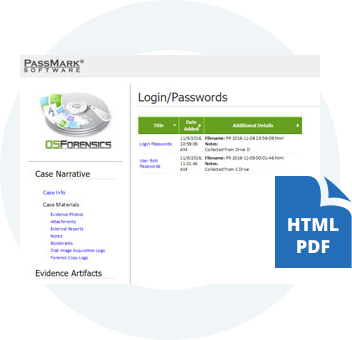

Create and recover disk images from evidence disks to support forensic analysis without compromising the integrity of the original data.
Re-create a complete RAID image from a set of RAID member disk images.
Create exact copies of the partitions or disks of an active system. Useful for live captures while OSF is running from your USB drive.


Professional and bootable edition
The professional and bootable editions of OSForensics have many features not available in the free edition, including:
- Import and export of hash sets
- Customizable system information collection
- No limit to the number of cases managed by OSForensics
- Recovery of multiple deleted files in one operation
- Listing and searching for alternative file streams
- Sorting of image files by color
- Disk indexing and search not limited to a fixed number of files
- No watermarks on web captures
- Multi-core acceleration for file decryption
- Customizable collection of system information
- Display of NTFS directory $I30 entries to identify potentially hidden/deleted files
- Memory viewer and dumper - kernel mode detection to bypass anti-dump tools
The bootable edition includes all professional features plus the ability to run on systems without a valid operating system. See the full comparison list between the editions.
Free Tools

ImageUSB
360 ° Case Management Solution. Manage your entire investigation.

OSF Mount
Identify evidence and suspicious activity through our hash matching

OSFClone
OSFClone allows you to quickly create or clone exact raw disk images regardless of the installed operating system.

Volatility Workbench
Identify evidence and suspicious activity through our hash matching
Technical Data
| Version comparison | Trial | Subscription Edition | Purchase Edition | Bootable Edition |
|---|---|---|---|---|
| Memory Viewer and Dumper | ✓ | ✓ | ✓ | ✓ |
| Raw Disk Viewer | ✓ | ✓ | ✓ | ✓ |
| Verify & Generate hash | ✓ | ✓ | ✓ | ✓ |
| Create and compare signatures | ✓ | ✓ | ✓ | ✓ |
| Zero drive & test | ✓ | ✓ | ✓ | ✓ |
| Drive Imaging | ✓ | ✓ | ✓ | ✓ |
| Mismatched file search | ✓ | ✓ | ✓ | ✓ |
| Hash Set Management | ✓ | ✓ | ✓ | ✓ |
| Search by filename | ✓ | ✓ | ✓ | ✓ |
| Scan for deleted files | ✓ | ✓ | ✓ | ✓ |
| File System Browser | ✓ | ✓ | ✓ | ✓ |
| Collect system information | ✓ | ✓ | ✓ | ✓ |
| Rebuild RAID Arrays | ✓ | ✓ | ✓ | ✓ |
| Hidden disk areas | ✓ | ✓ | ✓ | ✓ |
| Volume Shadow Copies | ✓ | ✓ | ✓ | ✓ |
| Email viewer | ✓ | ✓ | ✓ | ✓ |
| Registration Display | ✓ | ✓ | ✓ | ✓ |
| Prefetch Viewer | ✓ | ✓ | ✓ | ✓ |
| SQLite Database Browser | ✓ | ✓ | ✓ | ✓ |
| ESE Database Viewer | ✓ | ✓ | ✓ | ✓ |
| Plist property file viewer | ✓ | ✓ | ✓ | ✓ |
| $UsnJrnl File Journal Viewer | ✓ | ✓ | ✓ | ✓ |
| Detect user activity | Can only export 10 at a time | ✓ | ✓ | ✓ |
| Web browser screenshot | Image is watermarked | ✓ | ✓ | ✓ |
| Face Recognition | ✓ | ✓ | ✓ | ✓ |
| Python scripting | ✓ | ✓ | ✓ | ✓ |
| Cloud Imaging | ✓ | ✓ | ✓ | ✓ |
| Email Export | ✓ | ✓ | ✓ | ✓ |
| Forbidden image detection | ✓ | ✓ | ✓ | ✓ |
| Support for AFF4 file format | ✓ | ✓ | ✓ | ✓ |
| Web server logfiltering | ✓ | ✓ | ✓ | ✓ |
| Install and run from USB | X | ✓ | ✓ | ✓ |
| List and find alternate file streams | X | ✓ | ✓ | ✓ |
| Sort files by color | X | ✓ | ✓ | ✓ |
| Multi-core acceleration for file decryption | X | ✓ | ✓ | ✓ |
| Customizable collection of system information | X | ✓ | ✓ | ✓ |
| Import/Export Hash Sets | X | ✓ | ✓ | ✓ |
| Manage Cases | Limited to 3 cases at a time and a maximum of 10 items per case | ✓ | ✓ | ✓ |
| Disk Indexing and Search | Limited to 2,500 files or emails & 250 results per search | ✓ | ✓ | ✓ |
| Find Passwords & File decryption | Max. 5 passwords per browser type | ✓ | ✓ | ✓ |
| Recover deleted files | Limited to one file at a time. | ✓ | ✓ | ✓ |
| Show NTFS $I30 directory entries | X | ✓ | ✓ | ✓ |
| Runs without a valid operating system | X | X | X | ✓ |